- cross-posted to:
- smartphone_required@lemmy.sdf.org
- cross-posted to:
- smartphone_required@lemmy.sdf.org
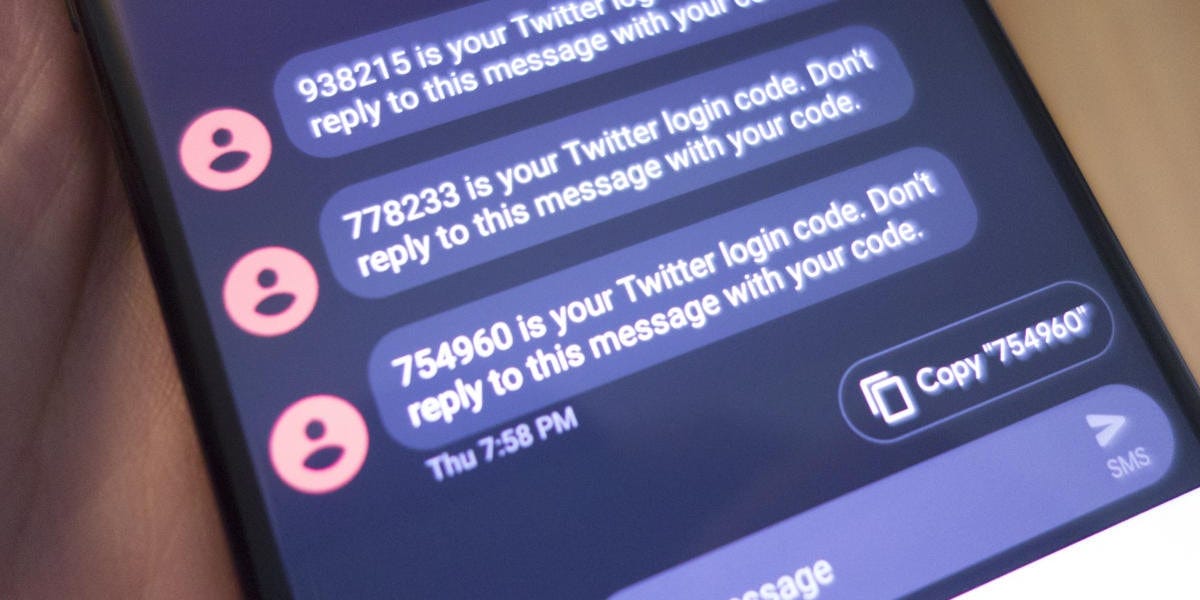
To the same audience: quit selling my fucking phone number!
I ditched a phone number I had for 10+ years because it was leaked everywhere. Only a few short months after updating my number with the DMV and a handful of other government agencies I started receiving scam calls/messages again.
At some point we need to adopt some fucking privacy laws. This is absolutely bonkers—is no one else fed up??
Edit: I already know how to silence unknown callers. What I want is to not have the problem in the first place, ideally by 1) having companies not sell personal data to third parties and 2) being able to block spoofed (non-encrypted) caller ID.
Oh everyone is fed up but we just elected a guy and government who is sure to make it all way way way worse.
He just helped put the nail in the coffin of the lie that crypto is for anything but scams, don’t worry, it’s gonna get real bad before it gets any better.
In South Africa, where I live, everyone is assigned an ID Number at Birth. You need an ID number, thumbprint scan AND proof of address to get issued a SIM card number due to a law introduced called RICA. It was meant to help fight crime. Worried that the government could listen in to calls or read their SMSs, the criminals just switched to WhatsApp, which also happened to become cheaper than SMSs and gained popularity in this time.
The cops never seemed to crack WhatsApp. The only drug busts that happen are when an open secret becomes laughably too open and when they harass every person arriving from South America at O.R. Tambo international airport just to catch the decoy mules carrying 12g of cocaine (total). Every dealer I ever organised with was over WhatsApp.
So now, woopsi, RICA stopped nothing and just became a liability. That treasure trove of fragile data made its way to scammers and spammers. A total net negative.
I’d encourage everyone else in other countries to apply major pushback to any government proposals in this direction.
Do people still believe that drug trade is ran by criminals?
I am pretty sure in every country, it is controlled either police or the spooks.
I am done pretending otherwise. Criminals are just useful idiots, the real thugs are the police and security apparatus
[citation needed]
https://en.m.wikipedia.org/wiki/CIA_involvement_in_Contra_cocaine_trafficking
This is just one example;)
there are MANY MANY examples don’t be a lazy pelican with your beak open. go look
The person who makes a claim has to back it up
stay ignorant and dangerous friend
Did we? My government leader hasn’t changed nor have we had an election lately
There’s a subset of Americans who are rather like ostriches: heads so deeply buried in the sand that they forget anything exists outside their immediate surroundings. Reminding them that the rest of the world is out there rarely has any positive results, however.
If they could read they would be upset by that.
“Bitcoin, it just seems like a scam,” Mr Trump said. “I don’t like it because it’s another currency competing against the dollar.”
— Donald Trump
Of course, Trump Coin made just for him is fine. And any security who bribes him. Oh wait now none of them are securities; Gary Gensler was our last line of defense.
[Edit: got it backwards]
I’m pretty sure a lot of scam calls use machines that call every possible phone number within an area code and see who answers. There is no way to avoid it.
this right here. I stopped getting scam calls years ago, I stopped answering and they just eventually stopped calling. If you don’t interact with the call (interact being ignore it or mute it NOT reject it) and it just goes to voicemail, they seem to eventually stop
Lucky you. I’ve been letting calls from any number I don’t recognize go to voicemail for years and nothing ever seems to change.
Setup a whitelist, I think it’s native on iPhone and there are multiple Android apps. Only calls from your contact list will ring through. My voicemail is, “You’re getting this because you’re not on my contact list, send a text and I’ll get back to you.”
I just block and report as spam any spam text messages I get and any calls that get marked as scam likely. It was terrible before the election because I live in a swing county in a swing state and I think everyone was just mass spamming every number in the area code, but since then I haven’t really gotten much, maybe one errant text every 2 or 3 weeks. Which is much better than it was last spring and summer when the amount started picking up for me.
If you’re job hunting, or work in specific fields this may not be a reasonable thing to do and that’s at least part of the problem.
This would deem troublesome yea, being said I firmly believe in separating work and home. I wouldn’t be willing to use a personal number for work related activities, at least not public related activities. Being said, I have no good solution for that, at least you are being paid for the scam call I guess.
Job hunting is what I meant. And you pretty much have to use your personal phone for that. I haven’t ever had a company phone. Doubt they’d give it to techs.
lists sourced from drivers licenses and motor vehicle registration records are literally sold by some states.
Source?
wisconsin literally has an opt-out/opt-in (based on your current status) box on vehicle registration renewal forms, for one.
Yep, wish I’d known that a couple years ago.
quit
sellingdemanding my fucking phone number!FTFY
Australia has a “do not call register”. It seems to mostly work, but telcos are having trouble with calls originating from outside the network with spoofed caller ID. We still get spam/scam calls from India among other places.
Even if they’re not calling you directly, they are still using your phone number to link you to things and create a shadow profile behind the scenes.
So does the US, though you need to re-register every so often. It works pretty well, but it’s not advertised very well.
Don’t worry, here in Europe we are full of privacy laws but I still receive tents of spam calls per day. Usually from non UE countries faking the number with my country numbers.
Anything with a London 020 number is guaranteed to be a man with an Indian accent pretending to be from British Telecom.
At some point we need to adopt some fucking privacy laws.
Yeah we absolutely had to ban TilTok because of privacy concerns but the idea of creating a law to protect our privacy is ridiculous beyond all reasoning. The stupidity of the United States government is absolute.
Agreed, but I’m not addressing TikTok specifically but rather policies similar to GDPR.
I set my phone to decline calls from unknown callers years ago.
These calls are already illegal. I used to report them to the FTC but I never heard anything back so I have no idea what happens, but I presume nothing. If I had the time to take them, and if they spoke English, I would record them with the Cube ACR app (which no longer works) and convince them to incriminate themselves. Ask their name, company, location, time/date, whether they ran my number through the DNC registry.
At some point we need to adopt some fucking privacy laws. This is absolutely bonkers—is no one else fed up??
Look at you, trying to use the government to solve every day problems that face pretty much all of us.
Don’t you know we only focus on gridlock issues to distract us from real issues now?
I do, unfortunately.
I have an app called Silence that lets me block calls from numbets not in my addreasbook. Highly recommended
https://github.com/x13a/Silence
Reminder: Dont blindly trust random internet sources!
That’s not the problem I’m referring to; this is already built-in to iOS (and I hope Android).
I’m confused of how this keeps happening to people.
Like I use my phone on most sites that allow it and I’ve never had spam/scam calls really, but I’ve also explicitly unchecked the marketing boxes that appear on the signup so maybe that it.
The last instance that actually happened to me was with entering my university a few years ago for my BS degree. They 1000% sold my contact information as some part of the deans/honors list process. I reached out to them and stopped that so fast.
deleted by creator
I’m sad PGP didn’t become a popular way to log into websites. A challenge-response protocol could have even been built into web browsers. Big tech is reinventing that idea as Passkey, but with a very big tech flavor.
deleted by creator
I’m already hearing about restrictions on exporting passkeys and some apps requiring that you’re not running a custom ROM on Android and stuff like that. Makes me worried they’re going to fuck that up and make it restrictive bs
Why should my OS be any of their concern?
From what I heard passkeys need google services framework for some reason. Don’t know technical reasons behind it but I would assume its bs given its google.
Yes, they don’t work without Google Play Services. Google didn’t implement passkeys in Android, only their own services.
I’m living this pain with a custom ROM already, with some banking stuff, Google Wallet, WhatsApp passkeys and I think Netflix (haven’t installed it) block you for tripping up Google’s security tests.
If passkeys become a big thing and they’ll start enforcing them and apps that have those security measures I’m going to fucking firebomb something. REEEEEE
Shit like this is why I don’t have a smartphone anymore. I have a brick phone that half the time I don’t even take out with me.
Passkeys or WebAuthn are an open web standard, and the implementation is flexible. An authenticator can be implemented in software, with a hardware system integrated into the client device, or off-device.
Exportability/portability of the passkey is up to the authenticator. Bitwarden already exports them, and other authenticators likely do, too.
WebAuthn relying parties (ie, web applications) make trust decisions by specifying characteristics of eligible authenticators & authentication responses & by checking data reported in the responses. Those decisions are left to the relying party’s discretion. I could imagine locked-down workplace environments allowing only company-approved configurations connect to internal systems.
WebAuthn has no bearing on whether an app runs on a custom platform: that’s entirely on the developer & platform capabilities to reveal customization.
Now type it a form that doesn’t allow copy and paste.
The California DMV requires you to renew your vehicle registration every year by paying with a bank account number (no card) which is like a 30ish digit number and they disable paste. If you get it wrong they won’t notify you in any way until you get pulled over by a cop who is one bad sneeze away from murdering you. It’s a great system.
Bank account numbers are, like, 8-10 digits. Certainly not 30ish.
What? Mine are 6 digits. Plus the routing number
Still, not 30ish digits like that person said. Hyperbole be damned.
I have renewed my CA registration with a credit card going back to at least 2016. A responsible driver would know their renewal failed when their registration document did not arrive via mail.
deleted by creator
Why?
Wdym why? That’s how most bank portals are designed. Copy-paste functionality is disabled and you have to type username, password, authentication code
I think my question was clear enough. The comment didn’t mention banks, I’ve never had a bank that did that, and we generally don’t try to hide our identities from our banks anyway. My best guess was that they misunderstood how public/private keys work, but since that was only a guess, I asked.
tbh ive never had a password box that I can’t copy/paste into
I’ve seen a few. They’re super annoying when trying to use a password manager with a decent password.
Can’t your password manager do autotype? That’s what I use mostly, because I don’t want all my passwords in my clipboard.
Probably. It works >99% of the time I need it so I haven’t poked around in the settings too much.
Or even just a paper form.
A bit of a hacky workaround on Android. Get Keepass2Android, use the included keyboard.
“Paste” whatever via the inbuilt password input functionality. It basically auto types out your passwords. (You protect this behind a master password/and optionally quick accessed by biometrics)
Profit
Yeah… I did this kind of thing before as a password and found that out the hard way
Thanks, gonna need your phone number to verify that though.
No you don’t! That’s why we have key-signing parties!
I want to preface this response saying I full agree with this, I want something like this to happen, I am responding because of some concerns I have. The real major one: How do you verify the authentication part of the data security chain?
A PGP key alone does not authentically validate that you are who you say you are. When the source is the untrusted party, it doesn’t accomplish the site’s goal. It’s the equivalent to me handing you a piece of paper saying “I’m John Smith and this is what I use to say I’m this” which works amazing for trusted exchanges, but when the source is “just trust me bro” it doesn’t solve anything for the website owner.
Websites get around this by having trust certificates/root servers that are co-signed with the PGP key. However, we lack any system like that for personal identities. Arguably, setting up such a system would isolate most of the known internet, as it is a significant roadblock, much like how SSL certificate usage was a huge roadblock for sites before Let’s Encrypt became a thing.
This setup would be amazing for logging into sites. However, it fails to accomplish what the websites that are asking for PII are looking for, which is verification that their user is who they say they are, and not a random third party.
To reliably use this setup, we would need something similar to Let’s Encrypt, but for user identification. The issue with that is it would become the de-facto attack vector (for both law enforcement and criminal parties), and that site would need to require PII to address the biggest concern on these sites, which is that you are who you say you are, and not Jo Smo or a bot looking to harvest data. Additionally, as mentioned earlier, a massive retraining of the internet would need to be done, which would mostly affect non-tech folk.
I am hopeful that an easy function that won’t violate users privacy comes out, but I don’t think the two topics are compatible sadly
The solution here is distributed trust by proxy. You start with a single exchange between two trusted peers, and build from there. As long as every individual link within the network is trusted, then any route between two disconnected endpoints can be trusted as well. As the network grows there is a very high statistical likelihood that there will exist many individual trust graphs between two nodes, which provides redundant validation.
I have always thought this would make a cool chat app. You enter the network by scanning someone’s QR code to become their validated peer, and then you can theoretically communicate with anyone else on the network by exchanging keys via trust graphs. You could then build a social network on top of it which shows you how many hops it takes you to get to some celebrity or some shit.
tox did something similar with this outcome, but it never took off. Basically with tox each account is actually stored locally, much like how Skype did when it was p2p, but the difference is your account is actually on your device, as in if you lost your “key” you lost your account, when you connected with others, you gave your friends your TOXID which was essentially your public key signature with some added information regarding what you wanted for privacy added to it, and then your messages were relayed through a p2p DHS network. Every communication was encrypted e2e. With tox anyone could create an account with any information, but only people you added were able to message you, and visa versa. The only time you were ever publicly disclosed was during adding contacts to people you didn’t already have, which helped minimize botting on it as bots wouldn’t be able to message you without your ID. The issue with that method was, both parties had to be online to message each other, there was no central server to manage identity and handle users, so every connection was considered trusted since you had to manually add the person via their tox ID.
I expect this solution /could/ be moved into a centralized system for all user accounts, since the only way to add people was manually adding their private key, but I would expect that on large scale, the lack of ability to actually stop problematic users might dissuade platforms from wanting to implement it, since account creation was as easy as just clicking “create account” and no accounts were ever verified server side, which in order to do, brings back to the issue topic: Privacy vs Security
How do they currently solve this problem for passwords? You could just have the register/create account button lead to a pubkey upload instead of a ‘set password’, no?
This problem isn’t addressing password authentication, its the website knowing who you are and that you are legitimate. Websites that collect things such as phone numbers during account creation don’t collect your PII as part of your password procedure. They collect it as a verification that you are an actual being and not a fake account/bot. The ease of being able to go through a forgot password thing is just a positive side effect.
This solution would work amazingly for logging in, there’s no argument for that, but it doesn’t address the elephant in the room: That the website wants to make sure you are a person/legitimate account and not a fake alias or a bot to scrape info, and when you are the only one providing that information that claim can’t be verified.
Nah, there are more than enough algorithms available that won’t work on quantum computers, I’m not too worried about that
-----BEGIN PGP MESSAGE----- hF4D7cLqolaUp8cSAQdAOCdAgwhjdDgwk6TsYbey9XLZrKT7ny+KRAORyTPJsmUw Fl1llKK3dYtwrPDUts8CA71uU8D2SOWwrk/mrQxlrP/btjNNj6j1vXehQJ0+FIuc 0sBPAU3onDQoAiPLDU7qky1cgtbgitMp4nGEnZ48Xh8OhWS03d9YfU4iIIuf/AWA MTzzbMLZCLqZrIiJGyE2EgJOLIMAOToxidQ6Z/blrT6W9effeu4GwEB622O0eIv5 ct0jm/e2A6j1Gf/7UsnzeC21ME55/JkDIFQQ5ZrYqRGp9+M0yNHXIhJXQvO+QmHz 1CclNIdwbnupIIy0+eiy+Wn41An/IUV2NJy+bmCxRmqTXZyNrfnPMrelY5imknd9 1oZGuHc6tWqNq0ntjV1sBBsxHtAXtFIBWcqEmUgnpxEBglRxx20thoWvQINisCB4 9ptHAUM9Qjr3tWFdvL5MqOHZ14XQ65bbKXhx5MJmr5yijA== =JKT0 -----END PGP MESSAGE-----No one except this guy will be able to read this. Die out of curiosity muhahahaha
deleted by creator
- Phone numbers
- social security numbers
Stop making personal information into digital ids because when it inevitably ends up in some kind of data breach. These companies all throw their hands up saying sucks to be you.
deleted by creator
Yeah, just generate a unique ID and ask only for the information you actually need.
What I hate is when they want you to store “secret” information like your mother’s maiden name/ first pet name for later verifications. You know these are stored in plain text of course. My own damn government does this stupid shit, and they’ve had several hacks of PII including gun registrations because as far as I can tell, nobody competent works in government IT.
I choose random questions and store the random passwords that I use as answers in my password manager. It’s also more secure because people can’t just Facebook stalk you for answers.
Security questions don’t care what you put in there. It’s not an exam. It’s basically just an alt password.
I just generate a string of alphanumeric text from my password generator and stuff those in there. If I lose my password vault somehow I’m cooked anyway, so.
I use bullshit answers for these, and save them in the notes section of my password manager.
Bane of my life as about a year ago my dad switched his sim and immediately started pestering me about not being able to log into his accounts.
Yes he got rid of the old number completly and expected me to somehow make his logins work. This is still going on to this day when he complains to me something doesn’t work it’s because he’s tied it to his old phone number.
It is the same thing that happened with US Social Security Numbers, which were originally just tracking numbers for that one purpose that were coopted by capitalists and treated like something special.
I remember I was flipping through some of my mom’s old college stuff and there was a club that she was involved with and everyone listed their address and social security numbers. It was wild, no idea why they felt the need to collect socials. But this was a very long time ago.
My college ID used to be my social security number, so maybe it was something like that? Iirc that’s no longer allowed in the US.
Good lord.
Imagine giving an institution like that your money.
It wasn’t that uncommon at the time. Take a look at this 2005 study the US GAO did on the issue: Social Security Numbers: Federal and State Laws Restrict Use of SSNs, yet Gaps Remain Also, this news article on the trend.
deleted by creator
999,999,999
It’s 1B. You’re forgetting zero.
Now I know your social security number. You fool!
It’s not just “capitalists” (whatever that means), every government agency seems to want it, employers and banks are required to ask for it, etc. It’s more than just “some people misused it,” we actually wrote it into regulations.
Please. It is the most annoying part of trying to use some sites and I rather not give out my number to people who store important info in plain text files.
Yes. Don’t forget your phone number will be exposed to the public when the business gets hacked.
Not if. When.
I’m in a quest to find a good email provider that doesn’t ask for a cellphone or another email address while creating an account, cock.li used to do this but now it’s “getting back on its feet”
Proton?
Just signed up for Tuta and they do not ask for this.
Tuta won’t let you check mail unless you give them a phone number or pay, if I recall correctly.
There used to be a way to make Google accounts with no number but that’s probably been patched. I generally refuse to add numbers if I can help it.
Proton, Mailbox & fastmail are all good options. Best way to avoid it is self-hosting but that is beyond most people (as in time-consuming).
If it’s associated with a specific device it will let you (ex my Android tv has its own account, no phone)
deleted by creator
Proton? More like pro Nazi.
OFTL Did they support Trump?
Their founder did, very openly and expressively, it was quite bizarre
Then he tried to walk it back by gaslighting.
“I wasn’t being political” said the man who was clearly being political.
The CEO made a remark about Trump, and used his corporate account for it.
If I recall correctly (no press statement was made by Proton), it was a personal remark on a corporate account, which he was quick to allow anyone to do. It also didn’t support Trump as a whole, just a remark Orangeman made about getting small business a level playing field (which I totally trust from an olicharch).
I’m still sticking with Proton for the foreseeable future, as its privacy awareness and advocacy is still a core business value.
Personally I use mailbox.org, it’s not free, but you are not the product
Selfhosted email I guess.
Is that even feasible without getting marked as spam by all the major players?
Hi, I recently set up my own email server
- It’s a huge pain in the ass getting things like DMARC and DKIM and whatever to work. Without those, most providers won’t even deliver your messages. But luckily, there are websites that help you check and fix your configuration
- Even once you do get these things set up correctly, most providers will send your outgoing messages straight to the recipient’s spam folder
- That being said, I believe most providers will mark you as “not spam” if the other person initiates the conversation. So this could be a non-problem if you’re making an email for your business and putting it on business cards or something.
- Mullvad (VPN provider) self-hosts their support email, and they seem to be doing fine.
Hope that helps
Yes. I host my own using Mailu.io. With the proper records, you will be able to send emails to any big email provider (proton, gmail, outlook). You need to pick a good TLD (.com, .net, .org, etc) so you don’t get your email thrown into the spam folder immediately.
If you buy a domain now, you will probably get on the Spamhaus blacklist, which every big email service seems to use (again, proton, gmail, outlook, and probably others), so you will need to wait a few months and keep a good spam record (well, don’t send spam emails obviously and keep your email server with the proper configurations).
Also, pick a good VPS provider (No vultr, no linode) with low levels of abuse, because if you setup your email server in an IP range with a lot of abusers, you may get your email flagged. (You can check that using https://www.uceprotect.net/en/rblcheck.php, but I’m not sure if uceprotect is trustable).
You can host your domain pretty much anywhere and they will provide mail hosting as part of most packages. From there, it’s up to you to talk to their servers to manage your mails, typically through IMAP.
Hosting companies will be whitelisted as far as mail routing is concerned.
create 2 proton mail account und use each other as a backup e-mail
Don’t u need an existing email to bootstrap that process.
nope, you can skip for the first account and then validate after the fact
I think you used to be able to “bootstrap” a proton account with a mail.ru account (which needs no prior email or phone), but I don’t think that works any more
How do you get DSL/coax internet when you can’t visit web pages?
Spoiler: With the good old telephone.
Ionos enabled me to do that.
But I chose not to.
Are Internet security and Internet privacy incompatible goals?
They are if the security is tied to knowing that an account is a person.
I don’t want to treat phone numbers as an ID, but for some reason my customers will give their phone number to me online far more willingly than they’ll cough up their email address, which is baffling only until you realize:
- Most people are technologically incompetent and are intimidated by the avalanche of crap they get in their email, and
- They never answer their phones anyway, so who cares?
I actually offer the option, because I don’t give a rat’s ass how people ignore me when I try to contact them. But when they place an order I at least need to be able to prove that I tried.
which is baffling only until you realize
I stopped being baffled when I realized most people are dumb as shit.
It’s just a fact of life, and we either see it or we don’t.
TBF many people are more intimidated by emails. My mum, for example, is in her 70s - she’s okay with using a smartphone but she doesn’t trust ‘internet stuff’. Won’t put her card details in, doesn’t trust emails - which is fair, because a lot of emails are bullshit or scams. She grew up with telephones though and feels safer using them. Possibly why so many phone scams target older people. I’ve tried to educate her.
This attitude doesn’t make people dumb. A bit ignorant, maybe, but I feel like ‘dumb as shit’ is a bit harsh.
When I give out my email, I always get spam, regardless of how many boxes I uncheck.
When I give out my phone number, sometimes I don’t
Of course that no longer makes sense since I have one phone number I can’t easily change, but give out uniquely generated emails that I can individually turn off
Yo sign me up 867-5309
Jenny, what is your area code?
I’ve been considering getting a pager or a burner phone just for this
Most phones are dual Sim these days
Better to not associate this number to your main phone anyway. Less likelyhood to have the info stolen from you.
Just get a virtual DID number from something like Voip.ms or virtualphone. There may be other providers out there that use crypto for payment for added privacy, but if all you want to do is be able to keep your real phone # off the grid, these work.
usually they check for VOIP numbers and give you an error. Has to be legit.
Never had that problem with the Google voice service
Yeah yeah it’s google, but it gives numbers that work
Last time I checked, Google Voice is only available for US residents. Not sure if there’s alternative.
Google voice is hit or miss. It’s worked for a lot of smaller sites for me, but the bigger / more corporate it is, the less likely it seems to work.
Can pagers receive text messages? I thought they are closed ecosystems, basically?
you know i’m not sure.
What i want is a phone that is basically a beeper for text messages. Doesn’t even have to send. just receive the stupid OTP. I wonder how hard that’d be to make with like a raspberri pi or something
Theres an LTT video where one of the boys intercept all Linus’ calls and texts, classic prank.
You mean the Veritasuim video with linus in it?
deleted by creator
On this question of verification, I don’t have a particularly foolproof solution, but maybe there just isn’t one.
I can criticize the modern web for a lot of things, but as long as we have situations where we want to check whether an account is a real person, as opposed to FarmingBot #295038, they need something. I’m not a fan of phone verification, but I’d only criticize it when we have alternatives.
I’d even be in favor of some kind of one-way algorithm by which a trusted real-person-identifying entity could tell a random third party site: Yes, this is a genuine human.
The technology has existed since the 80s.
X509 certificates would allow a government agency to sign a digital identity indicating that it’s legitimate, would allow for remote revocation in the event of loss or theft, and can be easily integrated with every existing computer and browser.
An issued physical card would resemble a credit card, with a chip in it. Other physical form factors can take the shape of USB-devices which bundle the card and the reader into a single device.
In the real world:
Also https://www.cac.mil/Common-Access-Card/, if the Americans are skeptical.
I don’t like the Austrian one being phone-integrated, but I understand why people would want that.
It’s because the phone is a two-factor token that everyone has with them. With a secure processor being the hardware token and fingerprints or face scans biometrics. This makes it ideal for saving such sensitive data. I most frequently use it to digitally sign documents in a legally enforceable way.
The card you linked is similar, and a smart card was one of the previous versions of our system. The goal here was to make it universally accessible, and a smartphone is perfect for that.
https://www.oesterreich.gv.at/en/id-austria.html
That exists and is better than a phone number.
Cool, now provide solutions that exist today for every other country
That is not my responsibility ;) I just shared that something like that exists.
Are internet security and internet privacy incompatible goals?
Yes. They are completely incompatible goals when anything relating to identity/being is linked to it. Examples of this could be anything from your name, to your behavioral patterns, to your phone number
Disregarding the entire possibility that ANY site is hack-able/breach-able, the issue stands that the reasons that most sites request PII is valid, for security reasons. There does not exist any valid method of ensuring users identity that does not violate users privacy. CAPTCHAS are proven inefficient, email domains are easy as a 1-2 click. Once the setup is done server side changing to a new address is as easy as changing your server settings and registering a new domain, then just pointing your MX records there. Heck depending on your postfix setup you might not even have to change server settings, if your account lookup is setup to ignore the domain and it all uses the same database. Even phone numbers have proven troublesome but its the least troublesome method available
The entire reason PII style setups are used, is because its an easy verification site side, but a hard to spoof verification customer side. Like the article says, phone numbers are hard to change for verification, many only let you change so many times in X period, and usually require some form of physical identity to register, and the ones who don’t are forced such as VOIP style numbers get blocked.
We lack currently a good system aside from that, because at the end of the day, how do you prove you are who you say you are, without disclosing your identity. I personally think it should be fine to give up some PII for security purposes, but this NEEDS to be restricted only to security and should never be shared with any entity, and this includes government overreach. Alas this will never happen.
This assumes a legitimate need to prove who you are outside the context of that specific site, rather than just within it. Sometimes that need is real, sometimes it is not.
When it’s not, and you only need to prove you are the same person who created the account, then a simple username and password is sufficient. Use 2FA (via authenticator app or key, NOT via SMS or email) on top of that. This allows users to prove to a sufficient degree that they are the owner of that account.
This is how most Lemmy instances work, for example. I can sign up by creating a username and password, with optional 2FA. They do not need my email. They do not need my phone number. They do not need my name, or my contacts, or anything else that is not related to my identity within their server.
I realize that this is untenable at large scales for any communications platform. Spam (and worse) is a problem wherever there are easy and anonymous signups. I’m honestly not sure how Lemmy is as clean as it is. I guess it’s just not popular enough to attract spammers.
You are correct with this comment yea, the biggest drawback (which as acknowledged we have seen on lemmy) is the anonymous of the account. It’s easy to spin up spam instances, and due to how federation works its hard to combat against it. I remember LW had an issue regarding that a bit ago with someone threatening to just keep changing domains to avoid blocking, which is indeed a problem for any of these style services. I agree at large scale, most sites are not going to want to have to put up with losing that level of control moderation side. It creates a lot of headaches and for most sites it’s just easier to enforce a policy that forces disclosing PII.
I absolutely love this.