I have all Firefox Data Collection and Use options disabled.
Anyone know what all of these services are doing? I assume they’re for auto updates, account sync, and maybe pushing Pocket ads and/or sponsored pins?
Likely, I’ll block most, but curious if anyone knew.
You can see the requests for Pocket, certificates and the captive portal check since those are in the actual url name. In addition to those, FF phones home for browser updates, extension updates, FF sync, safe browsing, etc.
I just googled a few URLs here, and found the following:
mozgcp.net is the Mozilla Google Cloud Platform, looking at the links it connects to, it looks as if it is accessing settings for Google, then finding some certificates, accessing pictures for the Pocket service and doing some product detection, why, I have no idea.
moz.works is Mozilla’s content delivery network, porbably nothing to worry about.
mozaws.net is probably a service running on AWS, the autopush service seems to deal with the Push API: https://developer.mozilla.org/en-US/docs/Web/API/Push_API
mozilla.com looks quite benign at first glance, but googling firefox contile tells you that that service is used to push ads on the new tabs page: https://mozilla-services.github.io/contile/
Detectportal is for captive portal detection, so that firefox knows if you need to log in on a captive portal before using the public wifi network you are connected to.
If that’s a stationary computer, that’s probably not needed, it can be disabled in about:config so it’s easier on the firewall
Awesome, much appreciated
mozgcp.net is the Mozilla Google Cloud Platform, looking at the links it connects to, it looks as if it is accessing settings for Google, then finding some certificates, accessing pictures for the Pocket service and doing some product detection, why, I have no idea.
Also Google Safe Browsing?
Sounds like it’s pretty standard, benign stuff. Luckily FF is open source, so if this freaks you out, then try one of the more private forks like LibreWolf. You won’t see these same connections there.
Fresh install of LibreWolf and it’s made a bunch of outbounds. Some seems related to it auto-installing uBlock. Others similar to default FF.
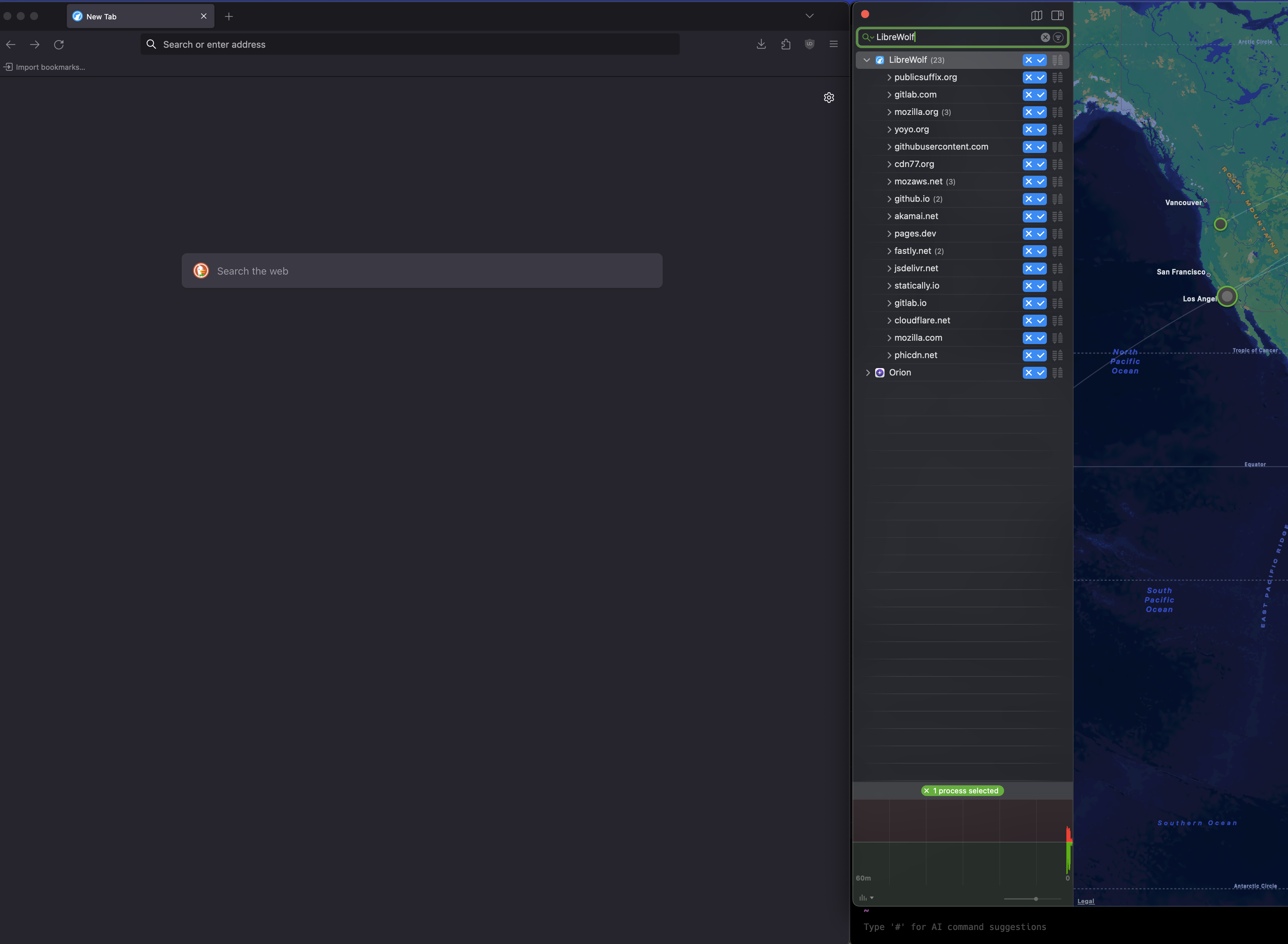
Looked up 2 of them, seems like they are settings and files, stored on Googles servers, but encrypted by the time it reaches Google.
Short of someone with a quantum computer, I doubt anyone will decrypt them, along with the billions of other user files out there. Suffice to say, don’t store/link anything sensitive if you’re worried.
Blocking might just break features, but be wary to see what’s broken based on what’s disabled and see if it can just be manually disabled in settings first.
I did see a reddit thread briefly talking about this, but wasn’t sure how accurate it was. Thanks!
No problem, I’m not exactly a fan of the cloud myself, but it’s being forced on us. It feels a bit like a fad, but I still store everything on secondary storage.
You don’t need a quantum computer, all you need is mitmproxy and some free time to set it up, and you can spy on the encrypted content of all your browser traffic.
How do you view these and how would you block them by the way? Via uBlock?
For my work machine I’ve got to use macOS. These connections were seen with the Little Snitch app. Highly recommend it.
gotcha! I’ve just started to use opensnitch (for linux) but I don’t usually inspect the detailed connections that often. thanks for the tip on firefox, I’ll be on the lookout for those.
Nice, would also recommend Safing Portmaster for Linux, if you’ve not tried it yet. A great FOSS tool for managing network connections.
thanks for the suggestion! will check it out!
Could be their google funding?
deleted by creator
According to their finance report, you’re technically correct. But they get 99% of their funding from a “search engine” company that stays anonymous. I can tell you it isn’t yahoo
Just use arkenfox user.js or librewolf. Firefox is a lost cause at this point. Mozilla doesn’t care about its users and keeps adding unnecessarily stuff. They blantantly lie about privacy when it takes hundreds of about:config preferences to make it remotely good in terms of privacy.








