Source Link Privacy.
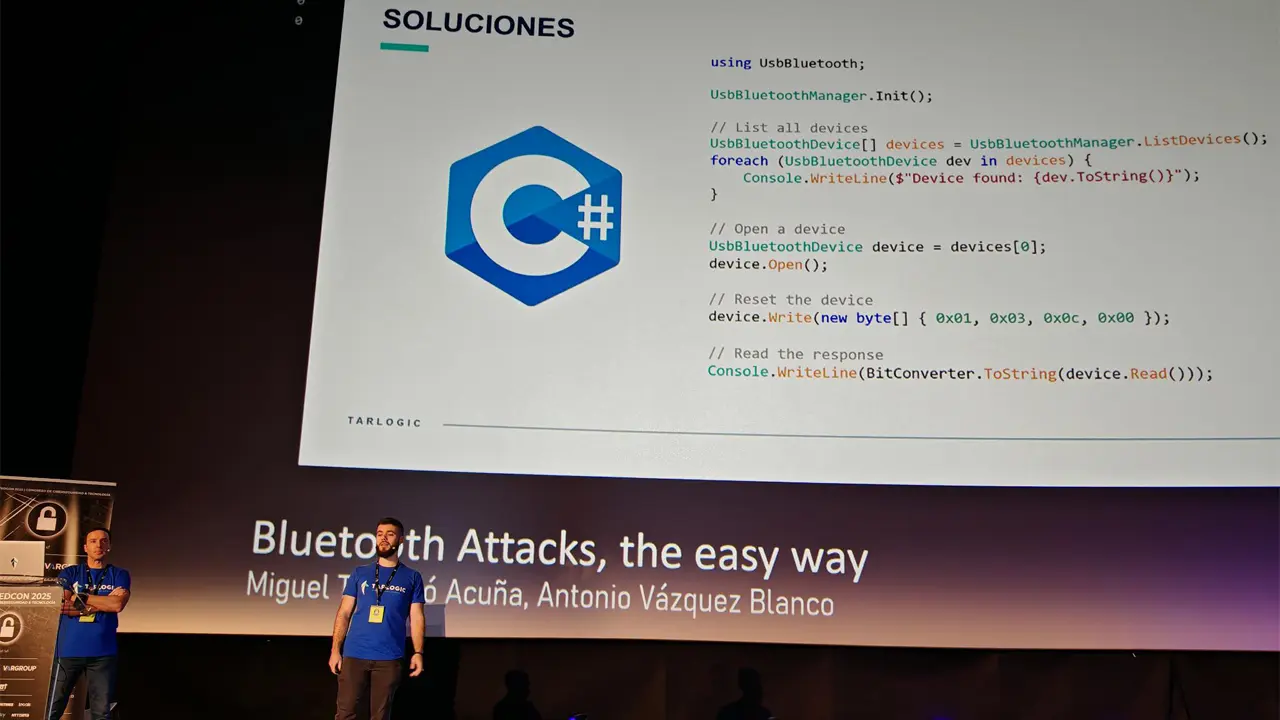
Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Update: The ESP32 “backdoor” that wasn’t.
Considering ESP32 is used practically everywhere on IoT devices, that’s really concerning.
I saw a comment somewhere that to exploit this a person has to be physically in the area (i think it was in a radius of few meters iirc). Thats not much better i guess since its not hard to be around random iot devices but it at least prevents mass attacks (if true).
I really haven’t seen any details. Most comments I’ve read indicate they think you already have to have access to the device and that this is just undocumented opcode calls. I.e. not a remote Bluetooth stack issue or remotely exploitable.
Given an opcode, as noted in the article (vague on details) and yes, I did read it. This doesn’t give me much cause for alarm.
Sounds like the attack is Bluetooth based itself.
So if somebody has command and control over any IoT device with Bluetooth…